One wrong move can have irreversible consequences, so remain vigilant.
Have you received an unexpected email from a legitimate wallet provider, such as Exodus or Metamask, informing you that your account/wallet needs action – sometimes as an urgent notice – otherwise, it will be suspended?
This is nothing new, although I have seen this become more prevalent again in recent months.
What’s most concerning is that we are not even in a bull market. Just imagine once we get into the next bullish cycle and more people enter the space, especially newbies.
Some will also be willing to participate in the self-custody of their BTC and crypto assets. This involved using a non-custodial wallet where you have full control (and thus, responsibility) of the private keys and recovery phrase to access your crypto wallets.
I’ll refrain from repeating information about NCWs, as I have covered this in previous pieces, notably this one.
https://medium.com/crypto-insights-au/non-custodial-vs-custodial-crypto-wallets-80a906c10535
If there’s one important takeaway message, it is this one:
Never share your recovery seed with anyone.
When you purchase a crypto wallet or use a desktop or mobile NCW, you should receive a prompt with this or a similar message. Here’s an example of a Trezor wallet recovery seed-phrase card containing this info.

Photo by rc. xyz NFT gallery on Unsplash
Some people might get this mixed up with multi-signature (a.k.a. multisig) wallets, whereby you need X number of signatures out of Y number of users – usually, a majority (2/3, 3/4, etc.) to approve a transaction.
However, this is different, and multisig works based on pre-determined agreements with trustworthy users, not some random person claiming to be a rep for a crypto wallet company or even a centralised exchange.
How to prevent falling victim to these fraudulent schemes
Whenever you receive an unsolicited email, the best thing to do is avoid clicking any links within and report it as spam/phishing. Over time, your email’s spam filters should identify those before reaching your inbox.
Checking the sender’s email address is often a good indicator of whether or not that email is from a legitimate rep. However, this is not a fool-proof approach, as some bogus messages can come from fairly convincing sources that appear legit but aren’t.
A logical way to approach this is, why would a rep from an NCW service contact me about my account being accessed or keys being compromised when the whole point of using the product is to have exclusive control over the crypto wallet’s private keys?
It might be slightly more plausible for a client when a crypto-exchange rep contacts them about their wallet. Then again, even if it were a staff member from your bank, they’d never ask for personal details via email or unsolicited message/phone call.
If you want to go a step further, you can report this scam email to the company mentioned in the email via their official email address, as listed on their website.
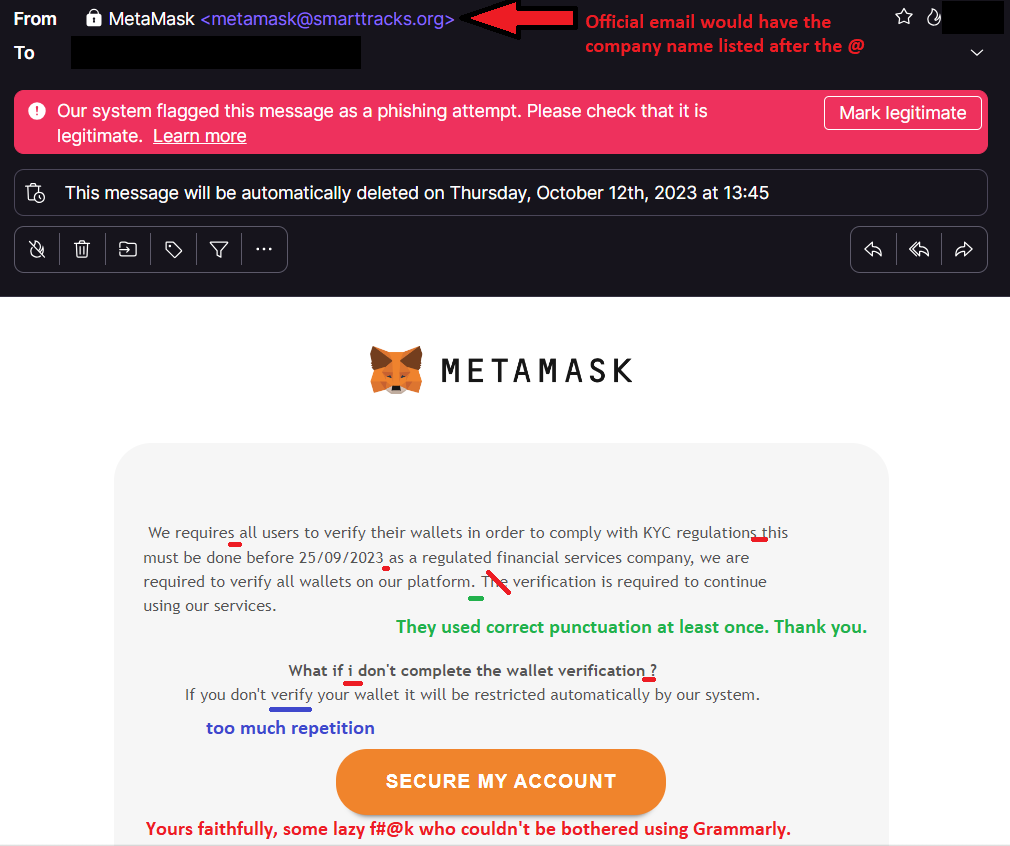
An example of a bogus email masquerading as a legit message (even though they did a s#!t job at it). However, some can be very convincing and use impeccable grammar and sensible word selection—source: The author (with amendments).
How do hackers get this sensitive information?
How do these pieces of s#!t manage to contact you in the first place? In many cases, it is due to your phone number or email address being involved in a hack at some point.
In other instances, it could be that you’ve mistakenly clicked on a link or attachment from correspondence that you thought was legit and were instead involved in a phishing scam.
Regrettably, most people have had some personal data accessed by hackers due to companies’ security flaws.
Negligence by an entity’s cyber security team for failing to implement the latest security updates or even a lapse in concentration when thoroughly screening any suspicious inbound messages can have catastrophic consequences, particularly with (but not limited to) sophisticated, state-sponsored hackers.
Where does crypto come into all of this?
Bitcoin has become a popular currency for hackers engaging in cyber ransoms, although Monero (XMR) and other digital assets have also been used.
Moreover, six wallets with 1,580 BTC in total have apparently been linked to hackers in North Korea.
Additional thoughts
With increasing regulatory requirements for strict know-your-customer, anti-money-laundering (KYC AML) laws for exchanges – alongside great monitoring of illicit crypto transactions by companies such as Chainalysis, Ciphertrace, Elliptic and Blockchain Intelligence Group – it will become more difficult for scammers and other malicious actors to obfuscate a crypto transaction trail.
In an ideal world, there would be a cryptocurrency system whereby regulations would also allow for (at least some) private transactions for law-abiding citizens whilst having KYC AML in place to avoid illicit activity.
This is similar to what we have today with cash for people who just want to buy regular items without having everything tracked; it is a double-edged sword, but cash still maintains its role in an increasingly cashless society, especially for marginalised people.
However, because a very small minority use crypto for criminal activity, these f#@kwits have to ruin it for everyone else in this space and tarnish its reputation.
Will regulators ever loosen KYC AML requirements for crypto? It is highly unlikely, if you ask me, particularly with privacy advocates’ unwavering support for crypto-mixing services such as Tornado Cash.
Tornado Cash was sanctioned in August 2022 for facilitating the laundering of more than $455 million worth of cryptocurrency stolen by Lazarus Group from various decentralized protocols.
Chainalysis blog, 23 August 2023
The tussle between libertarians and regulators will become amplified as the latter seeks to impose as many rules as possible to maintain sufficient control over crypto transactions, whether or not they’re justified.
In conclusion, you must always remain alert when dealing with dubious messages, not just when interacting with crypto wallets but with all online services.
If you ever have doubts about an email, contact the company directly through the official website (not via the details provided in the email), take a screenshot of the received message and wait for their reply before proceeding.
As the adage goes, “Better safe than sorry”, regardless of how much crypto is at stake.
Further reading
– The Chainalysis Crypto Crime Report 2023
– Chainalysis’ crime blog is mostly about monitoring crime in the cryptocurrency and distributed-ledger technology space.
Ciphertrace’s ‘Crypto Crimes & Anti-Money Laundering (AML) Report March 2023’
– ‘What is a Cryptocurrency Investigation?’ by Colin Connors, ERMProtect
Disclaimers
- N.B. None of this is financial advice; I am not a financial advisor. You are ultimately responsible for crypto investments, let alone in any asset class.
- The opinions expressed within this piece are my own and might not reflect those behind any news outlet, person, organisation, or otherwise listed here.
- Please do your research before investing in any crypto assets, staking, NFTs and other products affiliated with this space.
- For transparency, Bitcoin (BTC), Ethereum (ETH) and Cardano (ADA) collectively represent about 60% of my crypto portfolio.
Featured image by ozrimoz on Shutterstock

